Brands

Ordr Systems Control Engine
Take Control of Your Connected IoT and OT Systems
IOT IS EXPANDING FASTER THAN IT CAN BE SECURED
IoT and OT devices present unique challenges to access control. Common traits include:
– No user, No authentication
– Highly vulnerable — Typically run rudimentary or minimized versions of legacy operating systems without basic client protection software
– Closed systems — Minimal or no patching capabilities to defend themselves; installation of posture or other device management agents is rarely an option
– Susceptible to scans — Direct interrogation by profiling and other security assessment tools risky due to the fragile nature of device’s OS or network stack
Conclusion: Critical devices are vulnerable to service disruption, data theft, or compromise for ransom or serve as a launchpad for other attacks.
TAKE CONTROL OF YOUR ENTERPRISE
Ordr provides the most effective solution to identify, classify, and protect IoT and digital OT devices from unauthorized access and cyberattack:
– Passively discovers every connected device with high-definition detail-without the use of agents
– Automatically classifies devices with tags and maintains membership
– Quickly spots vulnerable and compromised devices so they can be quarantined
– Rapidly implements zone-based segmentation per NIST and IEC 62443 with AI-created firewall policies
– Continuously monitors device security risk and behavior
– Verifies segmentation policy is effective using simple, graphical tools
Take Control of Ordr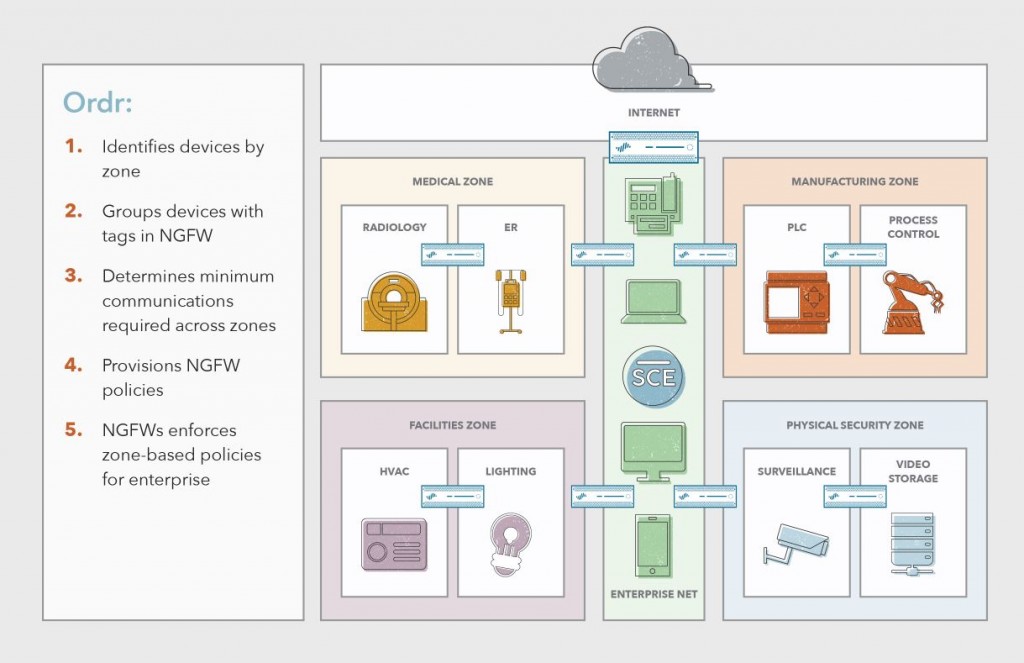
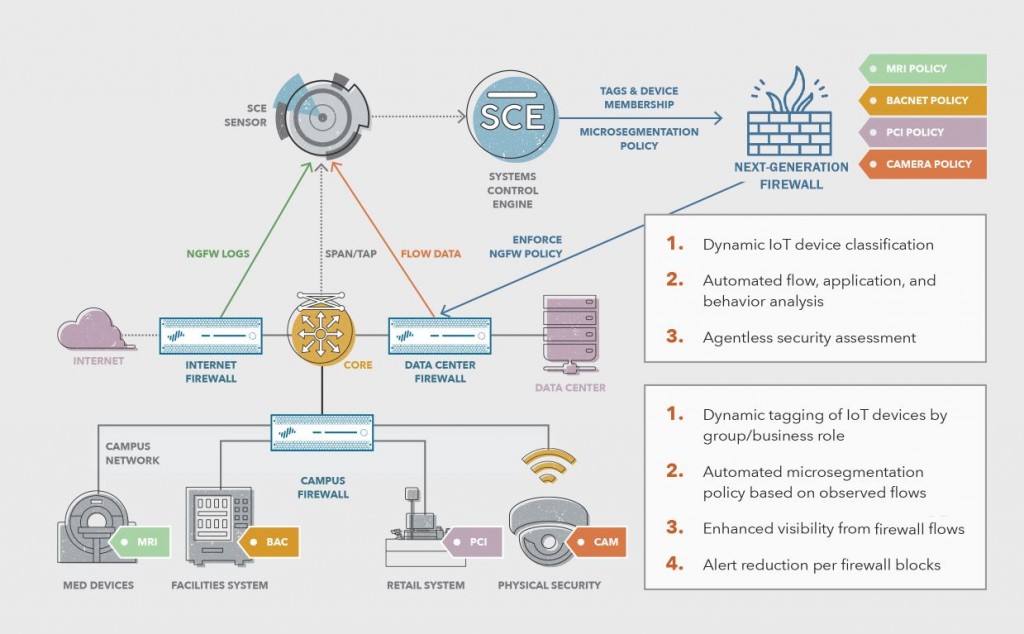
The most effective means to protect IoT and digital OT devices is through IEC microsegmentation and Zero Trust policy rules. Next-Generation Firewalls (NGFWs) provide scalable policy enforcement and segmentation controls for the enterprise. Ordr Systems Control Engine(SCE) discovers, classifies and groups all devices and automatically maps them into their respective zones, area, and cells using NGFW tags, and then dynamically generates NGFW security policy rules using these tags to deliver streamlined microsegmentation.
For example, building automation devices are seamlessly mapped to the Facilities Zone and facility devices within this zone are further segmented from each other. Security policy rules generated by Ordr are enforced by NGFWs to restrict access between zones, areas, and cells based on the minimum access required to allow devices to properly function while protecting them from insider or outsider attack. An HVAC system can talk with a trusted smart-building controller using approved protocols and applications by App-ID such as BACnet, but blocked from comunicating to the Internet or to another HVAC system.
Ordr SCE in Action
Ordr SCE integrates directly with the NGFW for multi-NGFW tagging policy enforcement. Ordr SCE Sensors provide agentless, passive data collection which feeds to Ordr SCE. Sensors may be centralized or distributed based on collection requirements. NGFWs can also act as sensors by sending rick flow data used to enhance visibility of localized traffic.
Ordr SCE analyzes the data to automatically discover and classify all OT, IoT, and non-IoT devices. It then maps groups of devices to existing NGFW tags or new ones auto-generated by Ordr SCE. When new devices are connected to the network, they are automatically classified and updated in NGFWs with the proper tag membership. Through its network and device awareness, Ordr SCE maintains current IP address information for tagged devices in NGFWs.
The Ordr Powered Solution
Providing advanced IoT device classification and tagging updates to NGFWs is only one piece of the puzzle. To move to microsegmentation and the enforcement of Zero Trust policy rules, administrators must understand which traffic to allow and deny. Ordr SCE provides this insight and fully automates the provisioning of security and segmentation policy. Alternatively, firewall administrators may leverage the auto-generated security policies as a reference to simplify manual update to security policy. Ordr SCE policy rules are translated into the syntax required to directly update NGFWs.
Ordr SCE’s job is still not done. While monitoring all devices for known threats and vulnerabilities, it is also keeping close watch on communication flows and anomalous traffic. Here Ordr SCE can reassign at-risk, vulnerable, and compromised devices to quarantine VLANs that map to restricted firewall zones. Attempts to access malware and other malicious sites are detected and correlated against NGFW logs to reduce criticality ratings for mitigated threats.
Together, Ordr and NGFW allows you to Take Control of your IoT and OT security by implementing segmentation access your hyper-connected enterprise.
About Ordr
At Ordr, we’re energized by the explosive growth in network-connected systems and devices. We recognize the tremendous opportunities that this represents for the hyper-connected enterprise. Improved delivery of care, efficient logistics and operations, quality enhancements in manufacturing, more stable and intelligent business-critical systems. We’re energized because we give you the power to take control and realize these myriad opportunities.